这两个源码我觉得可以记一下,这个考点可以给新生继续出题
Babywrite
先传.htaccess,,再用数组绕过写一句话,后缀为txt
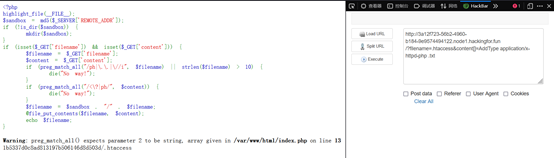
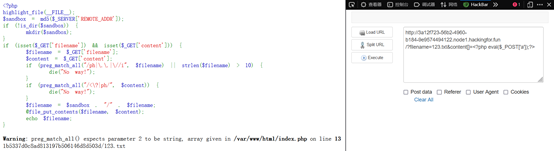
源码:
<?php
highlight_file(__FILE__);
$sandbox = md5($_SERVER['REMOTE_ADDR']);
if (!is_dir($sandbox)) {
mkdir($sandbox);
}
if (isset($_GET['filename']) && isset($_GET['content'])) {
$filename = $_GET['filename'];
$content = $_GET['content'];
if (preg_match_all("/ph|\.\.|\//i", $filename) || strlen($filename) > 10) {
die("No way!");
}
if (preg_match_all("/<\?|ph/", $content)) {
die("No way!");
}
$filename = $sandbox . "/" . $filename;
@file_put_contents($filename, $content);
echo $filename;
} phpmysql
换用Reflectionclass类
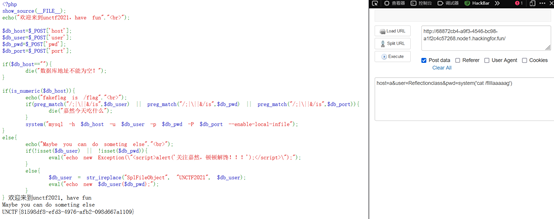
源码:
<?php
show_source(__FILE__);
echo("欢迎来到unctf2021,have fun"."<br>");
$db_host=$_POST['host'];
$db_user=$_POST['user'];
$db_pwd=$_POST['pwd'];
$db_port=$_POST['port'];
if($db_host==""){
die("数据库地址不能为空!");
}
if(is_numeric($db_host)){
echo("fakeflag is /flag"."<br>");
if(preg_match("/;|\||&/is",$db_user) || preg_match("/;|\||&/is",$db_pwd) || preg_match("/;|\||&/is",$db_port)){
die("嘉然今天吃什么");
}
system("mysql -h $db_host -u $db_user -p $db_pwd -P $db_port --enable-local-infile");
}
else{
echo("Maybe you can do someting else"."<br>");
if(!isset($db_user) || !isset($db_pwd)){
eval("echo new Exception(\"<script>alert('关注嘉然,顿顿解馋!!!');</script>\");");
}
else{
$db_user = str_ireplace("SplFileObject", "UNCTF2021", $db_user);
echo $db_user;
eval("echo new $db_user($db_pwd);");
}
}